FieldHash:
Offline-Verifiable Evidence for
Long-Horizon Data Integrity
Quantum-derived fingerprints + post-quantum signatures. Verify locally, even when networks or vendors are down.
The Problem: Why Crypto Alone Isn't Enough
Long-horizon data (5–100+ years) can outlive today's cryptography.
Harvest-Now/Decrypt-Later (HNDL) makes archives captured today exploitable tomorrow when quantum computers mature.
Insider abuse and supply-chain compromise mean that—even when signatures verify—provenance can be manipulated at the source. Signatures prove possession of a key, not how content was produced.
Dependency outages leave verification systems unavailable precisely when trust checks matter most.
The consequence (why it matters now)
Auditors increasingly ask, "Can you still prove this exact artifact in 10–30 years?"
HNDL risk means encrypted data exfiltrated now may be readable later.
When signers or build pipelines are compromised, "valid" certificates can still represent untrue data—and long retention requirements amplify every vulnerability.
Two Pillars (Why Teams Choose FieldHash)
Operational continuity (offline): Verify locally on endpoints with no external calls—workflows keep moving during outages, maintenance windows, or in air-gapped networks.
Cryptographic assurance (future-proof): Post-quantum signatures (NIST ML-DSA/Dilithium) plus optional physics-anchored evidence when hardware is used; clear, policy-labeled trust tiers (Strict / Standard / Offline).
FieldHash Solves This by Adding Physics-Anchored Evidence That Complements Cryptography
When you issue certificates, FieldHash captures quantum-execution fingerprints (when hardware is used) with device provenance and calibration context. Verification remains fast, local/offline, and policy-aware, backed by evidence that's impractical to reproduce without equivalent quantum hardware, parameters, and conditions. Simulation fallback is supported and clearly labeled as a lower-trust tier.
Where verification runs: On your endpoints (Windows/macOS/Linux), offline, using the signed evidence bundle and local policy—no quantum access or third-party validators required.
What FieldHash Delivers
-
Quantum-Anchored Provenance (When Hardware Is Used)
When hardware is used, certificates include device/backend IDs, job references, distribution digests and noise statistics, and calibration snapshots—creating a time- and device-bounded fingerprint that's impractical to reproduce without equivalent hardware, parameters, and conditions. Provider metadata is included when available; offline verification does not depend on provider access.
Post-Quantum Binding + Vault-Only Custody
Evidence packages are signed with NIST ML-DSA (Dilithium). Private keys remain inside Vault/KMS/HSM (no application-memory egress). Optional Kyber KEM envelope is policy-gated for encrypted attachments.
-
Local Verification, No Network Required
Verifiers don't need quantum access. They validate the signed evidence package locally and apply versioned profiles (Strict / Standard / Offline). Evidence contains hashes/statistics only—no raw document content.
Fail-Open Overlay
If issuers or providers are unreachable, your workflows continue unchanged; verification can occur immediately offline or later from cache. No blocking dependencies on FieldHash services.
Efficient Distribution
Evidence is content-addressed and supports ETag/304 revalidation to avoid redundant downloads at scale.
-
Secure-by-Default Ingress
Production enforces client mTLS plus short-lived JWT, least-privilege RBAC, intelligent rate limiting, and abuse protections. PII-aware logging protects observability pipelines.
Optional Transparency Log
Off by default. Certificates remain fully offline-verifiable without it, preserving privacy while enabling additional auditability when required.
Vault/KMS/HSM Custody
No private key egress to application memory.
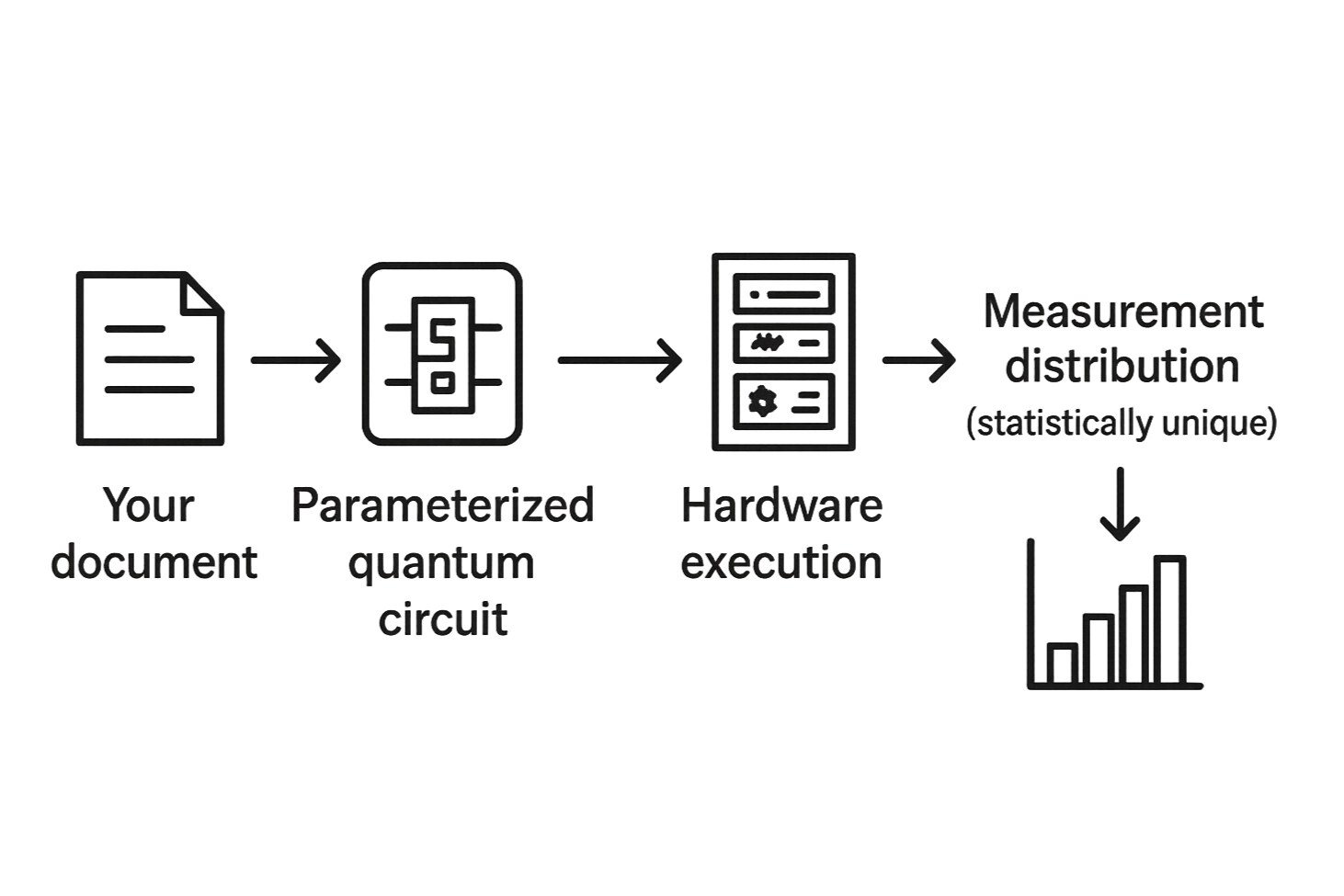
How it works (at a glance)
Hash — Bind content with SHA-256 (primary) and SHA-512 (audit trail).
Execute — Run a parameterized circuit on IBM Quantum or Quantum Inspire (when configured), or simulation (clearly labeled).
Fingerprint — Derive distribution digest + noise statistics; capture calibration snapshots when hardware is used.
Sign — Seal evidence with NIST ML-DSA (Dilithium) via Vault/HSM; optional NIST ML-KEM (Kyber) for encrypted attachments.
Verify — Anyone can verify locally; profiles enforce minimum shots, drift windows, and hardware/simulation mode policy.
Distribution efficiency: Evidence is content-addressed and supports ETag/304 revalidation to avoid redundant downloads.
Where it fits
Healthcare & Life Sciences
Clinical trial integrity and consent management for long-term compliance.
Why FieldHash: Quantum-anchored certificates (when hardware is used), vault/KMS/HSM signing, offline verification, and PII-aware observability.
Why it matters: Offline verification satisfies audit checks during outages; no new inline dependencies on EHR workflows.
Deployments: Managed or on-prem; air-gapped simulation for enclaves; transparency optional and off by default.
Finance & Public Sector
Long-horizon records that must outlast multiple crypto generations while meeting evolving audits.
Why FieldHash: Physics-anchored evidence + post-quantum signatures; local/offline verification; posture flags for auditors (mTLS/JWT/Vault).
Why it matters: Trade continuity during verifier outages; HNDL mitigation with NIST-selected PQC; provenance checks that resist supply-chain compromise.
Deployments: Multi-region, on-prem, or hybrid; ETag/304 for efficient evidence distribution; optional transparency where required.
View finance & public sector use case
Legal & Compliance
Evidence packages that withstand courtroom scrutiny with offline verification and clear trust tiers.
Why FieldHash: Signed evidence (distribution digest, noise fingerprint, calibration snapshots when hardware is used) plus deterministic profiles (Strict / Standard / Offline).
Why it matters: Trust checks remain enforceable offline; no vendor dependency for long-term validation.
Deployments: Enterprise or air-gapped verification; package formats compatible with review workflows.
View legal & compliance use case
Defense & Critical Infrastructure
Strict profiles; on-prem/air-gapped deployments when quantum access is restricted.
Why FieldHash: Hardware-backed evidence for high-assurance profiles; simulation fallback clearly labeled for development/training.
Why it matters: Zero key egress; fail-open design preserves mission continuity; provenance checks resist insider/supply-chain threats.
Deployments: IL/Fed environments, enclave installs; evidence distribution via controlled channels; posture flags for operations.
View defense & critical infrastructure whitepaper
AI & Content Provenance
Prove synthetic content authenticity with quantum-anchored evidence.
Bind an artifact's digest to a hardware-measured fingerprint plus device provenance and calibration context.
Minimal metadata, maximum privacy: use digests (prompt/parameters), model/process IDs, and timestamps. Optional C2PA assertion; COSE/CBOR or VC packaging.
Key Custody & Trust Distribution
Vault/KMS/HSM custody: Signatures are created inside your security boundary; no key egress to application memory.
Trust bundle / JWKS: Public keys + policy delivered via a signed trust bundle (GPO/Intune) or internal JWKS endpoint for connected enclaves.
Trust tiers (policy-labeled): Strict typically requires hardware; Standard/Offline allows simulation, always clearly labeled.
What's Live in v2.5
✓ Quantum backends: IBM Quantum® & Quantum Inspire; policy-driven failover with clearly labeled simulation fallback and hardware-first profiles.
✓ APIs (v2): Issue, verify, revoke; fetch evidence/metadata with ETag/304 caching for efficient distribution.
✓ Security: Client mTLS, JWT, RBAC, tenant quotas, rate limiting, and Vault-only signing/unwrap to keep private keys out of application memory.
✓ Validation: 636 automated unit tests + 56 integration tests covering certificate lifecycle, disaster recovery, observability, and multi-tenant isolation.
✓ Observability: Prometheus metrics (including PQC posture counters), OpenTelemetry tracing, and structured logs with PII controls.
✓ Deployment: Containers + Helm charts; cloud, on-prem (air-gapped via simulation), or hybrid topologies with documented SLOs and DR drills.
Threat Model (Summary)
HNDL (Harvest-Now/Decrypt-Later): Adversaries capture encrypted data today to decrypt later when quantum computers mature. FieldHash mitigation: NIST ML-DSA (Dilithium) signatures resist quantum attacks; evidence remains verifiable without re-encryption.
Insider/Supply-Chain Compromise: Valid signatures can attest to untrue provenance when signers or build pipelines are compromised. FieldHash mitigation: Acceptance is bound to measured execution (distribution + noise fingerprint); forgery requires equivalent hardware, parameters, and conditions.
Dependency Outages: Verification must succeed offline to preserve continuity during network or vendor failures. FieldHash mitigation: Evidence packages are self-contained; verifiers operate locally without network calls.
Why Teams Choose FieldHash
✓ Physics-anchored evidence complements post-quantum cryptography—raising the cost to forge provenance beyond practical limits.
✓ Local, offline verification—no vendor lock-in for long-term validation; evidence bundles are self-contained.
✓ Non-exportable key custody—signing inside Vault/KMS/HSM boundaries; zero key egress to application memory.
✓ Clear trust tiers—Strict requires hardware evidence; Standard allows simulation (clearly labeled); Offline optimizes for air-gapped review.
✓ Fail-open design—if FieldHash is unavailable, workflows continue unchanged; verification can occur later with cached evidence.
FAQ
-
No—simulation is supported and clearly labeled by policy. Strict profiles typically require hardware; Standard/Offline allows simulation.
-
On your endpoints, offline. Verifiers validate the evidence package locally using versioned profiles—no network calls required.
-
FieldHash combines client-side offline verification, NIST-selected post-quantum cryptography (ML-DSA/Dilithium), explicit trust-tier labeling (hardware vs simulation), and—when hardware is used—physics-anchored evidence, all in a portable, self-contained bundle.
-
Yes, FieldHash v2.5 (release tag v1.0) includes:
Comprehensive test coverage- 1,720+ passing tests with 64.6% code coverage and enforced coverage gates
- 226 test files across multiple categories: 170 unit, 16 integration, 25 production, 2 API, 1 E2E, 1 CI
- 3,297 test functions covering certificate lifecycle, disaster recovery, multi-tenant isolation, PQC signature validation, and observability
Integration infrastructure- 7 Docker Compose configurations (api, monitoring, observability, stack, cbp, integration)
- Setup/teardown automation, reusable test helpers, and container orchestration
- 12 GitHub Actions workflows for CI/CD including nightly tests, coverage reporting, container security scanning, and production tests
Disaster recovery validation
- Automated backup/restore flows against PostgreSQL and Vault
- Persistent circuit-breaker state across restarts
- Multi-region failover testing
Security hardening- Client mTLS, JWT/RBAC, rate limiting (100 req/min), tenant quotas
- PII-aware logging with redaction policies
- Vault-only key custody (zero private key egress to application memory)
- Non-exportable signing keys in HSM/Vault
Observability- Prometheus metrics with PQC posture counters (enforce_pqc_vault_signing, require_client_cert, demo_enabled)
- OpenTelemetry tracing for distributed request tracking
- Structured logs with PII controls and tenant isolation
- Latency SLO validation (health < 1s, issuance < 5s, signature-only verification ~ms, full verification seconds-scale per profile)
Audit-ready documentation
- Comprehensive test and operations evidence with 64.6% coverage
- Coverage reports (module-by-module breakdown)
- CI/CD strategy and deployment runbooks
- Evidence manifest for compliance audits
Get Started
Schedule a Demo →
Read the v2.5 Public Whitepaper →
Production deployments • IBM Quantum and Quantum Inspire integration • NIST-selected post-quantum cryptography • Designed for decades-long data integrity